Deployment scenarios
SuperOffice can be set up in several ways to suit your business needs and security requirements. The three most common scenarios are described below in increasing order of security.
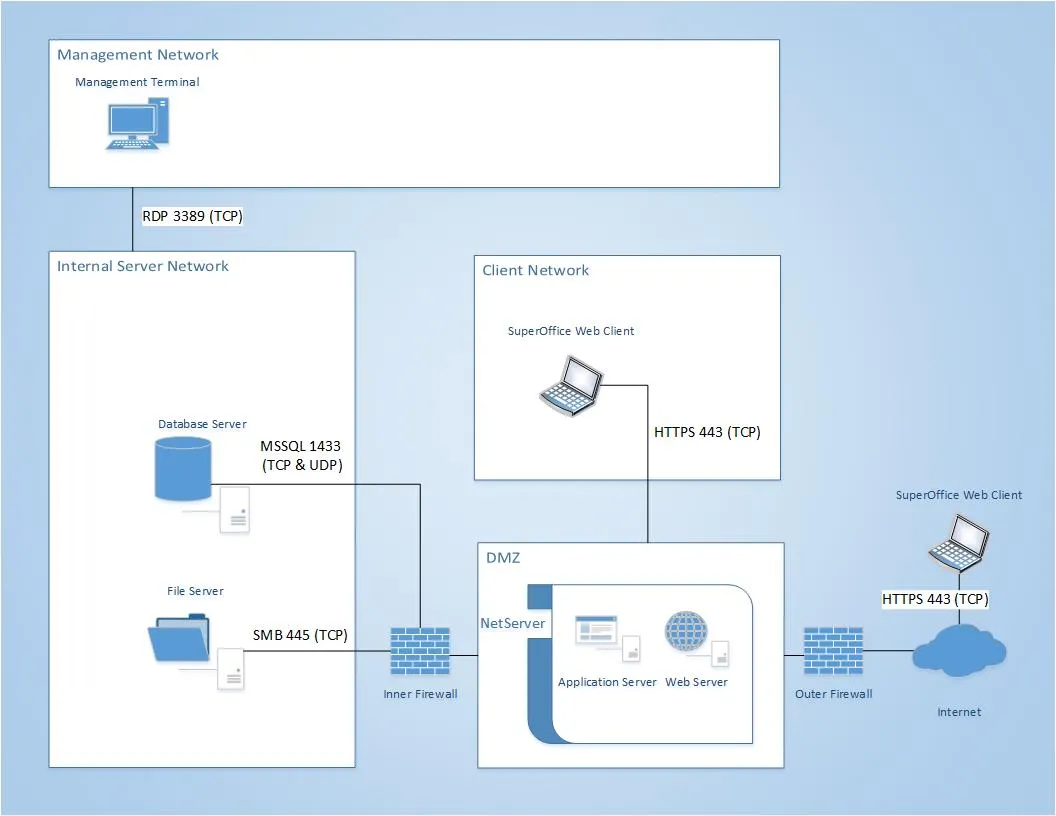
Scenario 1: Directly accessible from the internet
In this scenario, SuperOffice is available from any location when connected to the Internet. The Web / NetServer is placed in the DMZ and is accessible from the Internet. This is the least secure setup as it exposes the Web / NetServer to attacks from any other server in your DMZ that may become compromised.
Scenario 2: Directly accessible from the internet through a proxy
Instead of making the NetServer directly accessible from the Internet we recommend placing a reverse proxy in the DMZ to forward traffic to and from the Web Server. This proxy server isolates the Web Server from the Internet and allows us to inspect and filter web traffic to and from the Web Server using a web application firewall.
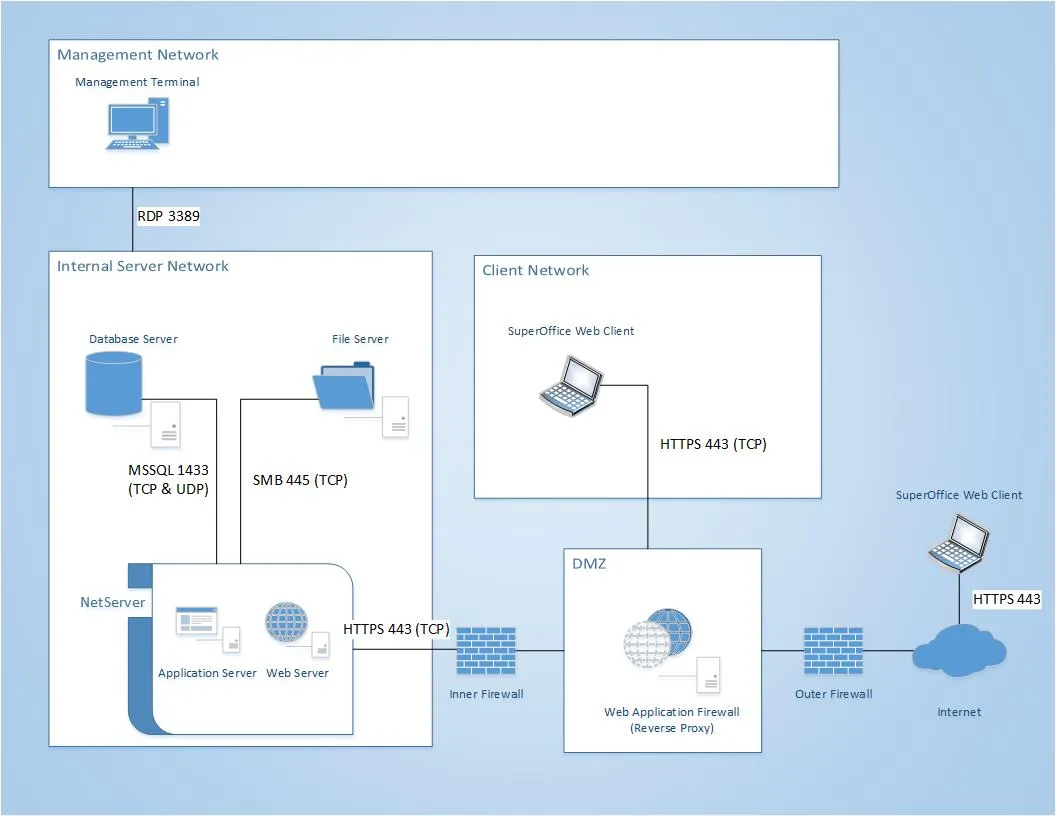
Scenario 3: Internal only
In this scenario, SuperOffice is only accessible from IP addresses inside your business network. This is the most secure way to deploy, as it does not expose SuperOffice to the public internet, minimizing your company’s attack surface. It would still be possible for employees on travel to access the system using a VPN connection.
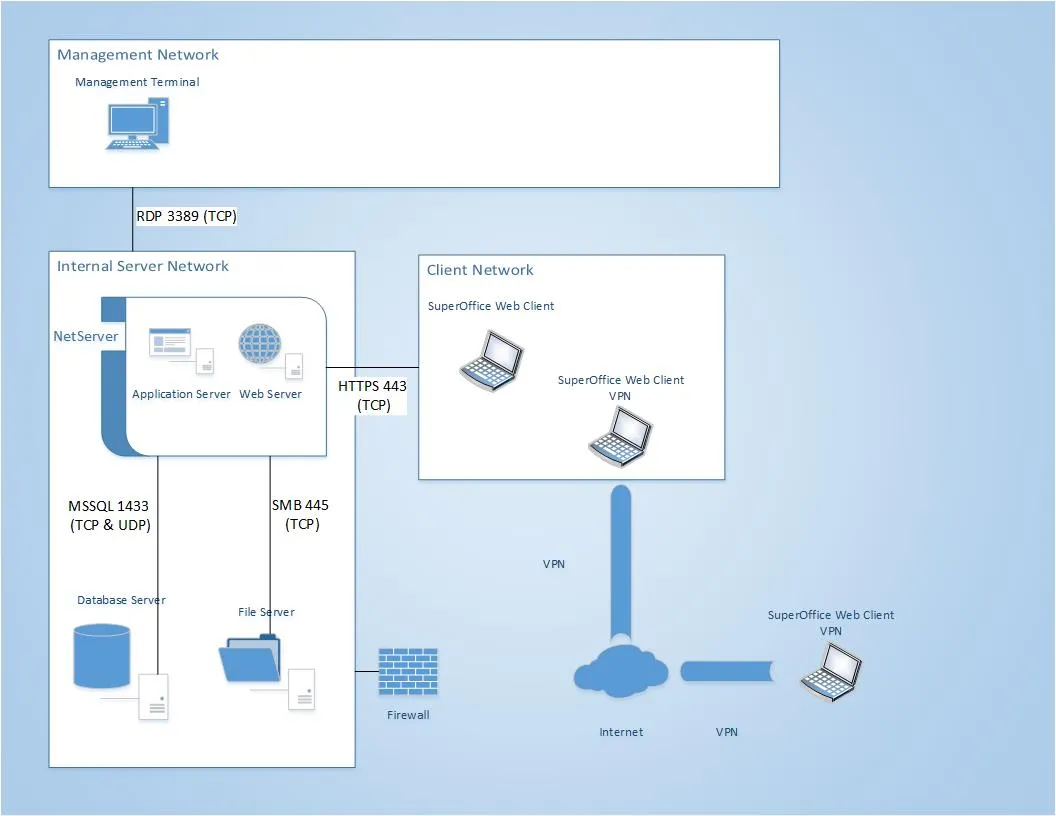
We do not recommend using the Windows client without a VPN connection as this exposes SMB-traffic over the internet and requires an insecure firewall configuration. Instead, we recommend using the web client with a secure HTTPS connection to the webserver.